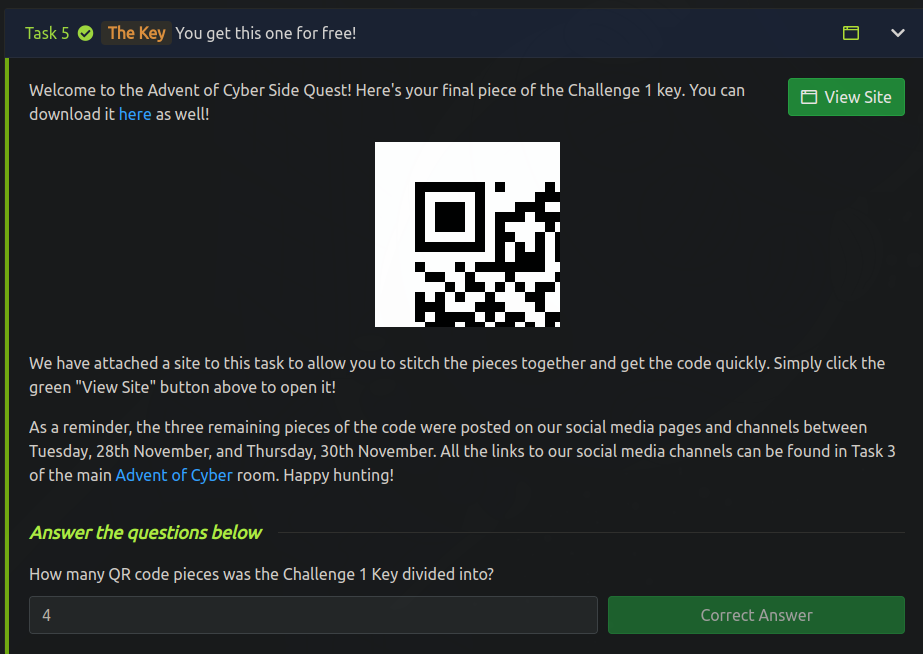
Introduction
This year, TryHackMe has released a Side Quest alongside the main Advent of Cyber event. The side quest consists of four rooms with difficulty from Hard to Insane. During the event, each of those rooms was accessible only by finding a hidden key located in:
- First Side Quest Challenge Key
This key is divided into four parts. Three will be posted on our social media channels between Tuesday, 28th November and Thursday, 30th November. The final part of the key will be posted in this room, on December 1st, 4 pm GMT. Find them all, put them together, and uncover the link to the first secret challenge! All the links to our social media channels can be found in Task 3 of the main Advent of Cyber room.
- Second Side Quest Challenge Key
This key will be hidden in one of the challenges of the main Advent of Cyber event between Day 2 and Day 8. Look for clues to find out which challenge to dig into!
- Third Side Quest Challenge Key
This key will be hidden in one of the challenges of the main Advent of Cyber event between Day 9 and Day 16. Look for clues to find out which challenge to dig into!
- Fourth Side Quest Challenge Key
This key will be hidden in one of the challenges of the main Advent of Cyber event between Day 17 and Day 24. Look for clues to find out which challenge to dig into!
Now that we’ve said all of that, let’s find out where those keys were hidden!
First Side Quest Challenge Key
We already know that Key 1 is split in four and one of the key pieces is in this room.
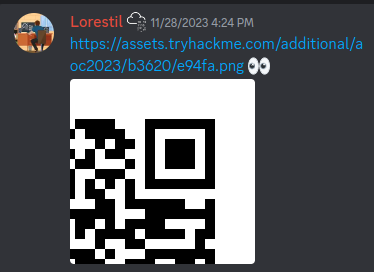
As for the rest of the places, we need to look through THM’s social media. Starting with Descord, I another piece of the key as a pinned message in the aoc-23-side-quest channel posted by Lorestil.
The third piece was hidden in a link given in a post on LinkedIn. Also, 🥚👀 was placed before the link, which made me think that the last piece of the key will have the same format.
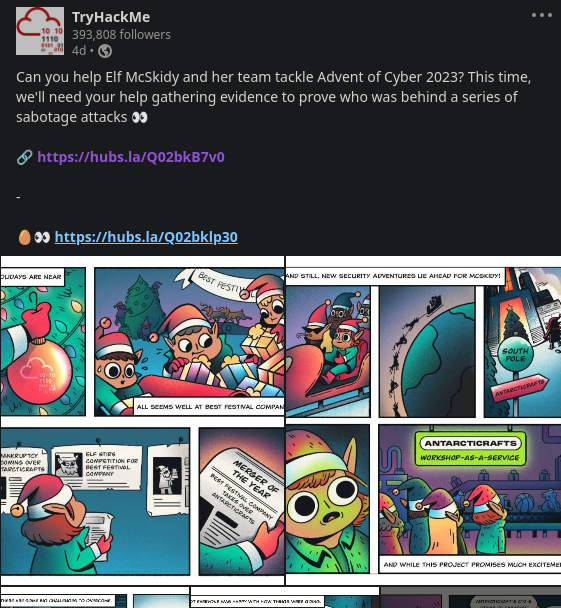
And, as expected, the last link was on a Twitter (X) post.
https://x.com/RealTryHackMe/status/1730184898365767880?s=20
After parsing all four, we get the link to the first Side Quest Room.
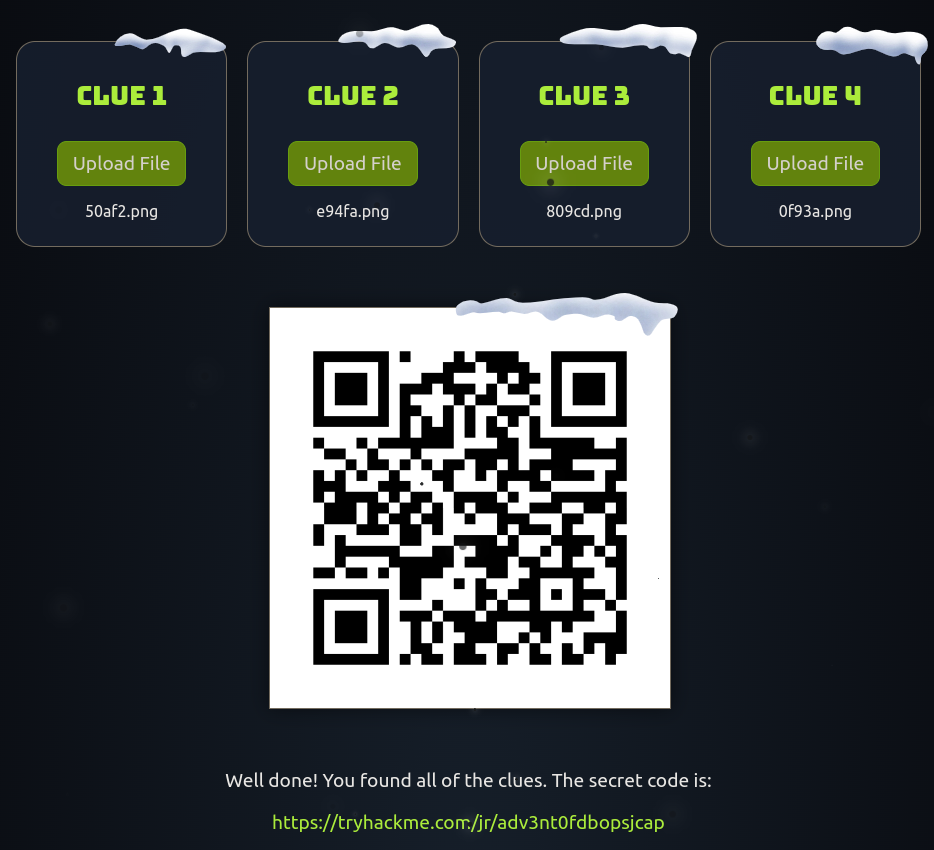
https://tryhackme.com/jr/adv3nt0fdbopsjcap
You can find a walkthrough of the room here.
Second Side Quest Challenge Key
The Second Key was hidden in Advent of Cyber’s Day 6 task, “Memory Corruption: Memories of Christmas Past”. A good note is that the game from this task is very similar to the game from Task 15 in Advent of Cyber ‘22. Now, “luckily” for us, this task covers WebAssembly and how to use the tool Cetus, which is what we are going to use to manipulate the vulnerable buffer.
I would advise completing the task before searching for the key.
To start, let’s take a look at the actual source code of the game by opening the Developer Tools, navigating to “Sources” and selecting “index.wasm.gz”. If Cetus has already been installed, the file will be in the wasm folder. After making a quick search for the word “yeti” (Ctr-F), we can see a very long line with some sentences that were never used in the game.
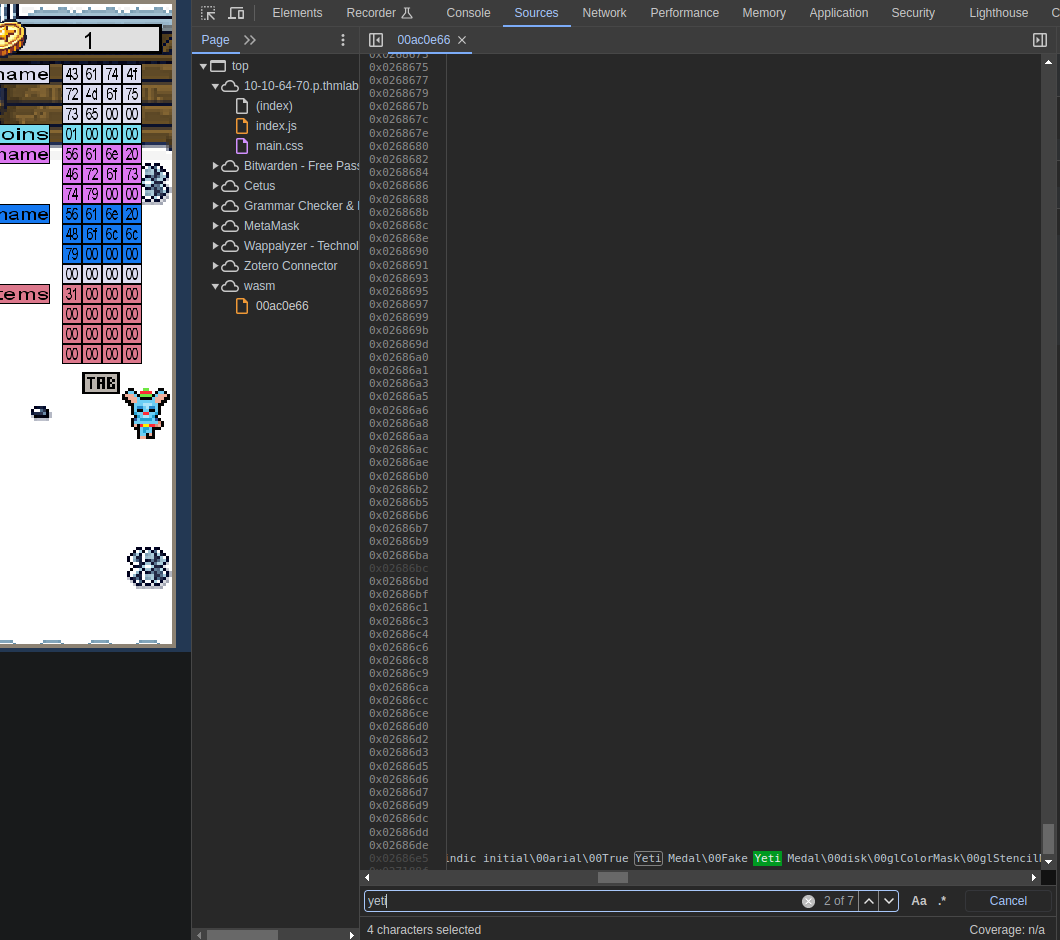
After analyzing the information from this line, I discovered the following details provided by the so called Glitsh:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
I'm... the G-gglitch of Chri5tm4s Pa___st
I hHunt this g---ame s1nce its creati0n. Didn't y-u bellllieve the Frostlings?
This 1tem w@s f0rb1dden l0ng aGo... How d_d you ev3n gGet it??
You h0ld th3 bBbadge ___ of th3 Y3t1!
How come you don't speak glitchy anymore?
According to the legend, a cat named Snowball will arrive at this place one day
He will meet with Midas the greedy merchant, and Ted the name switcher
He'll bring exactly 31337 coins and the token of the Yeti
When all these conditions are met, input the 30 lives secret code and what's hidden shall be revealed
True Yeti Medal
Fake Yeti Medal
So we now know we need to meet the following conditions:
- Change the name of our avatar to Snowball.
- Change the greedy merchant’s name to Midas.
- Change the name switcher’s name to Ted.
- Change the coin count to 31337.
- Set the token of the Yeti in the inventory.
- Input the 30 lives secret code.
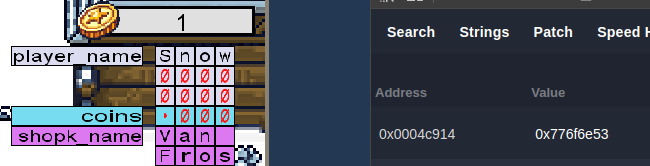
While we can use the buffer overflow and change those values via the name switcher, it would be difficult to set the NULL values. Therefore, we can find the addresses holding those values by using the Cetus search. In this example, I used the first 4 bytes of the name value to find the first address and then searched for the range of addresses as each address is supposed to increase by 4, meaning that the last invetory address should be 0x4c94c.
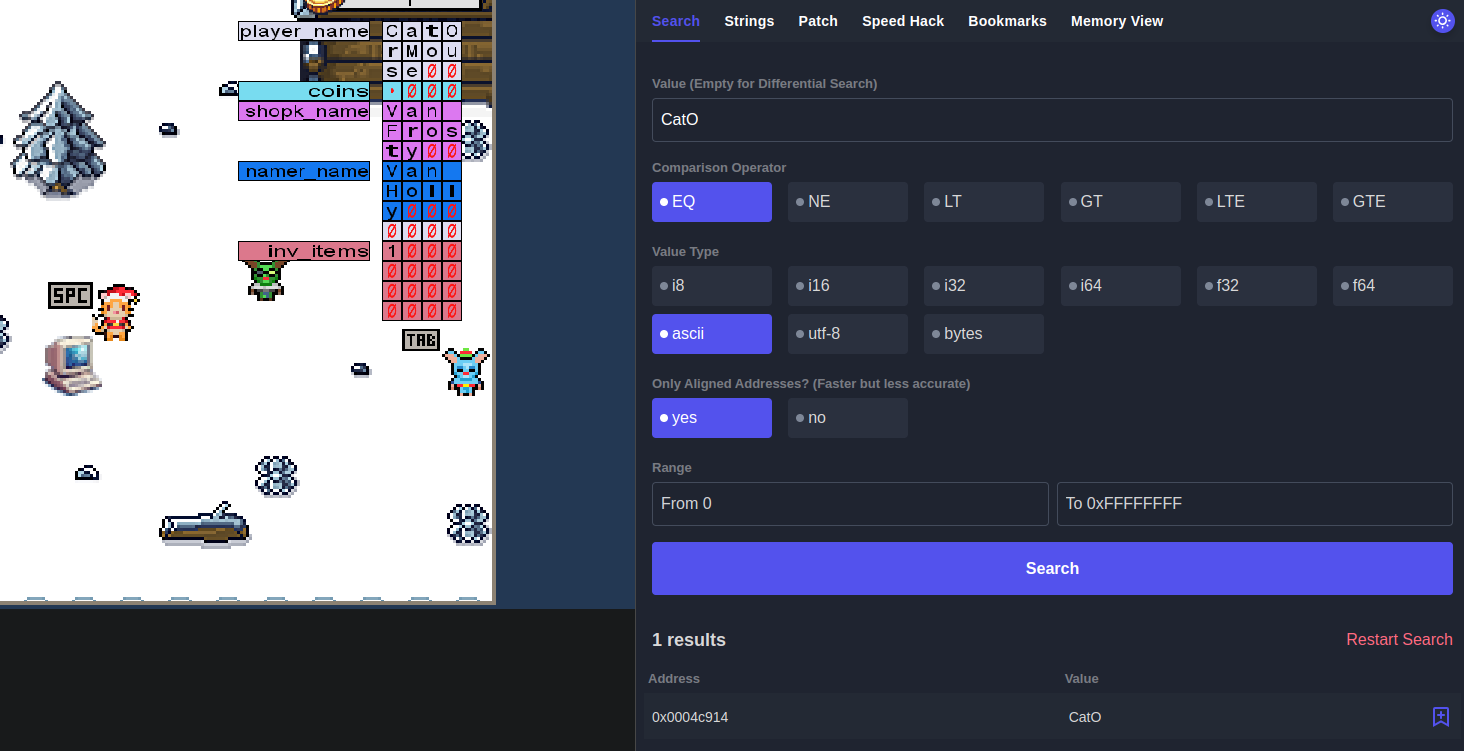
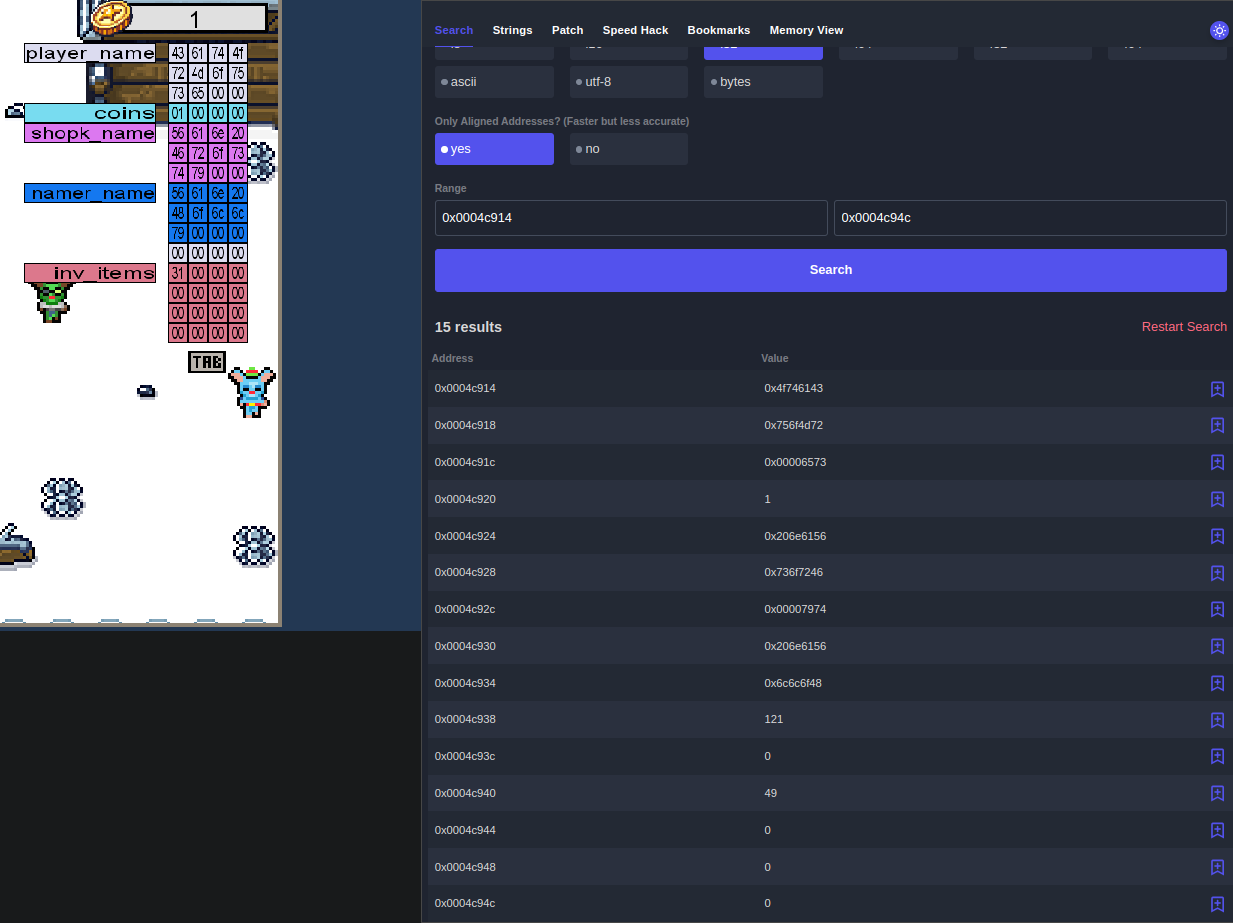
Now, with those addresses bookmarked, we need to fulfil the conditions. To do this, we convert each character from ASCII to HEX and then reverse it due to LSB (Least Significant Bit).
E.G.:
Snow = hex(w), hex(o), hex(n), hex(S) = 0x776f6e53
Now via the help of Python, we can convert the values we need:
1
2
3
4
5
6
7
8
9
10
11
12
def string_to_lsb_hex(input_string):
# Convert string to hexadecimal
hex_representation = input_string.encode('utf-8').hex()
# Reverse the order of hex pairs
reversed_hex = ''.join(reversed([hex_representation[i:i+2] for i in range(0, len(hex_representation), 2)]))
return reversed_hex
conditions = ["Snow", "ball", "Mida", "s", "Ted"]
for i in conditions:
value = string_to_lsb_hex(i)
print(f"{i}: {value}")
1
2
3
4
5
Snow: 776f6e53
ball: 6c6c6162
Mida: 6164694d
s: 73
Ted: 646554
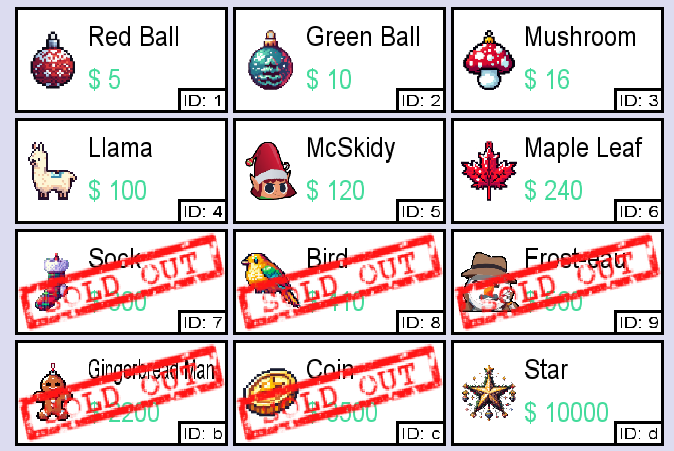 The coins are stored as an integer. That being said, there is no need to convert them by hand, as Cetus can do that for us.
The coins are stored as an integer. That being said, there is no need to convert them by hand, as Cetus can do that for us.
We need to fulfil the final condition, which is to obtain the token of the Yeti. As it can be seen from the merchant, every item has a unique one-byte ID ranging from 0x00 to 0xFF, which gives us 256 possible options for the Yeti’s token ID. We can perform a brute force search, which will review that the token ID is 0x10.
Overall, we need to place the following values in the following addresses:
| Description | Address | Value |
|---|---|---|
| Player Name 1 | 0x0004c914 | 0x776f6e53 |
| Player Name 2 | 0x0004c918 | 0x6c6c6162 |
| Player Name 3 | 0x0004c91c | 0x0 |
| Coins | 0x0004c920 | 31337 (0x00007a69) |
| Shop Name 1 | 0x0004c924 | 0x6164694d |
| Shop Name 2 | 0x0004c928 | 0x00000073 |
| Shop Name 3 | 0x0004c92c | 0x0 |
| Namer Name 1 | 0x0004c930 | 0x00646554 |
| Namer Name 2 | 0x0004c934 | 0x0 |
| Namer Name 3 | 0x0004c938 | 0x0 |
| Invetory 1 | 0x0004c940 | 0x10 |
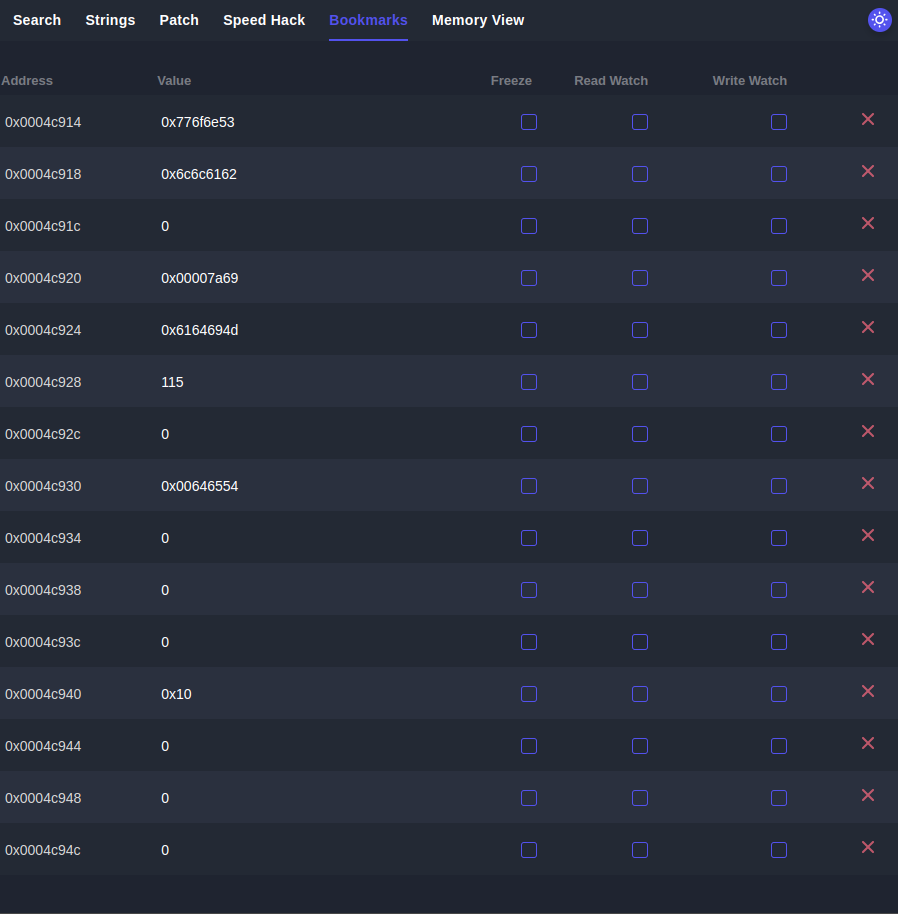
And finally, we need to enter the 30 lives secret code. After a quick search, I found this key combination which seemed to work:

After executing the code the game “glitches” and the Yeti appears with our Second Key.

https://tryhackme.com/jr/armageddon2R
You can find a walkthrough of the room here.
Third Side Quest Challenge Key
The Third Key was hidden in Advent of Cyber’s Day 11 task, “Active Directory: Jingle Bells, Shadow Spells”. The hint this time is:
Van Sprinkles left some stuff around the DC. It’s like a secret message waiting to be unravelled!
After reviewing the content of the Administrator\Desctop directory, we can indeed see some files other than the flag. In this case, I used Evil-WinRM’s download function to download the files for further analysis.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
*Evil-WinRM* PS C:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/22/2023 10:56 AM chatlog_files
-a---- 11/22/2023 10:29 AM 11620 chatlog.html
-a---- 10/16/2023 7:33 AM 17 flag.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> download chatlog.html /home/nick/chatlog.html
Info: Downloading C:\Users\Administrator\Desktop\chatlog.html to /home/nick/chatlog.html
Info: Download successful!
*Evil-WinRM* PS C:\Users\Administrator\Desktop> download chatlog_files /home/nick/
Info: Downloading C:\Users\Administrator\Desktop\chatlog_files to /home/nick/
Info: Download successful!
So, it appears that the chatlog.html contains (surprise, surprise!) a private chat between McGreedy and Van Sprinkles. Furthermore, we can see that Van Sprinkles had sent the key we were looking for by accident. Later, he deleted the original message with the attached picture and sent a cropped version.
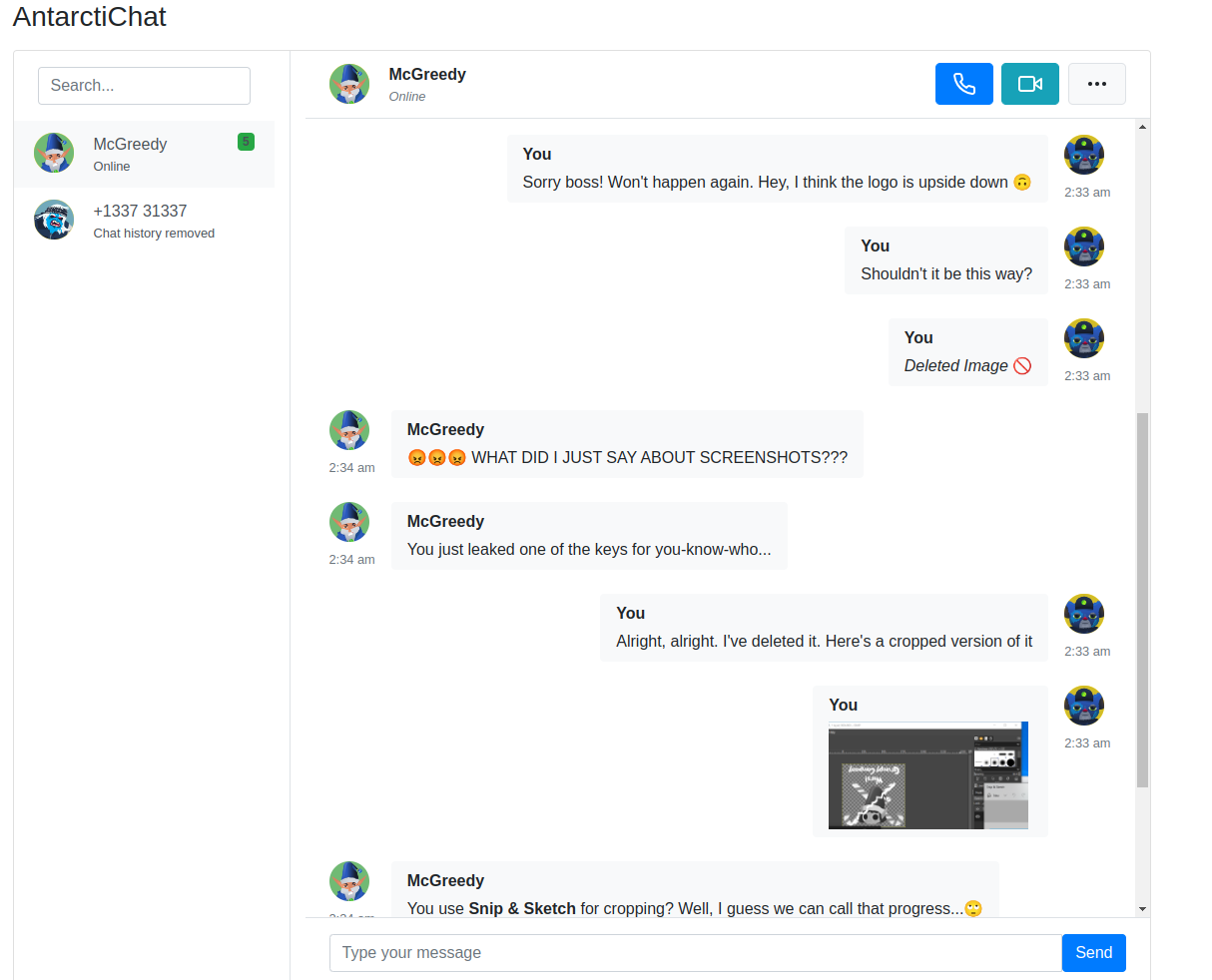
Seeing that McGreedy has sent a message about the cropping tool choice specifying “Snip & Sketch” in bold looks a little bit like a hint, so I tried to find what can be done with a cropped image.
Shortly after, I dioscovered Acropalypse – CVE-2023-21036 and the perfect tool to exploit it – Acropalypse-Multi-Tool.
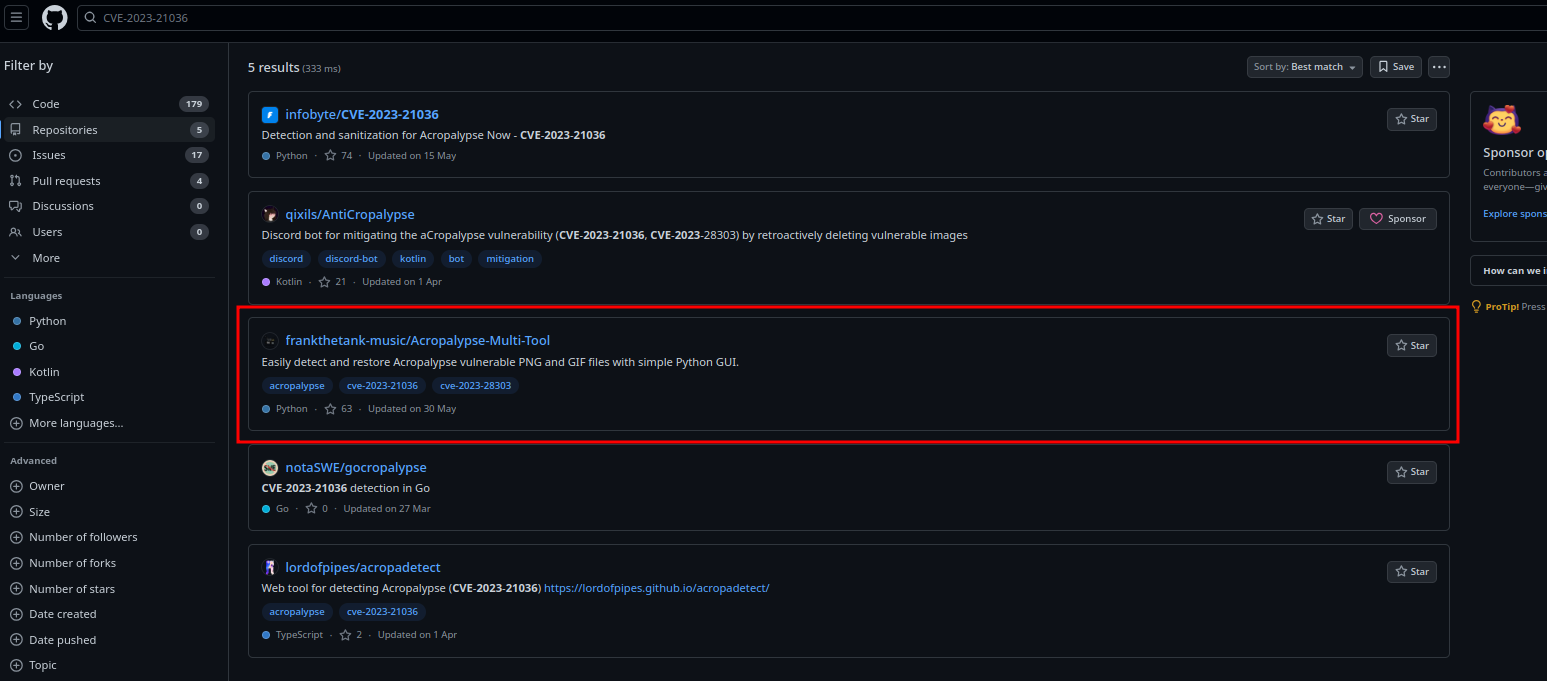
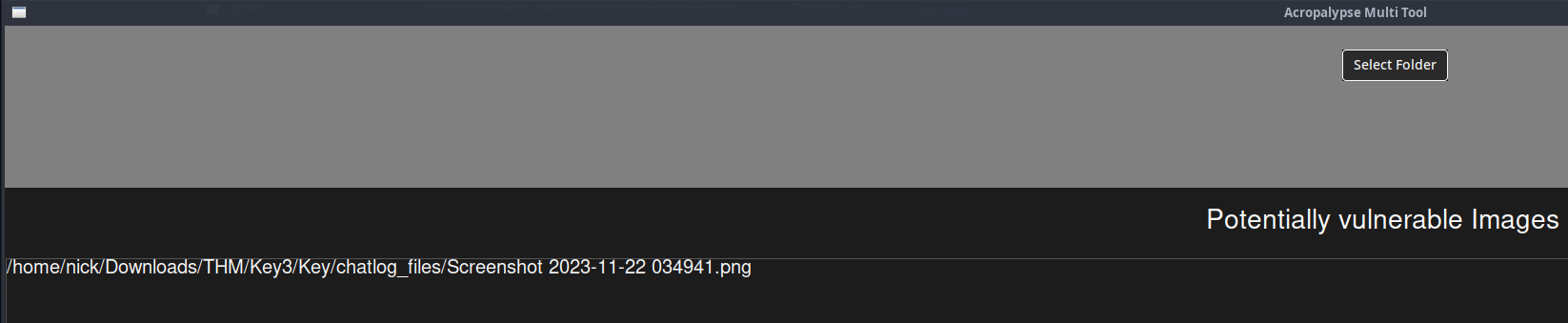
So, I first did a test to the directory where all of the images from the chats are stored. No surprisingly, the cropped screenshot appears to be vulnerable.
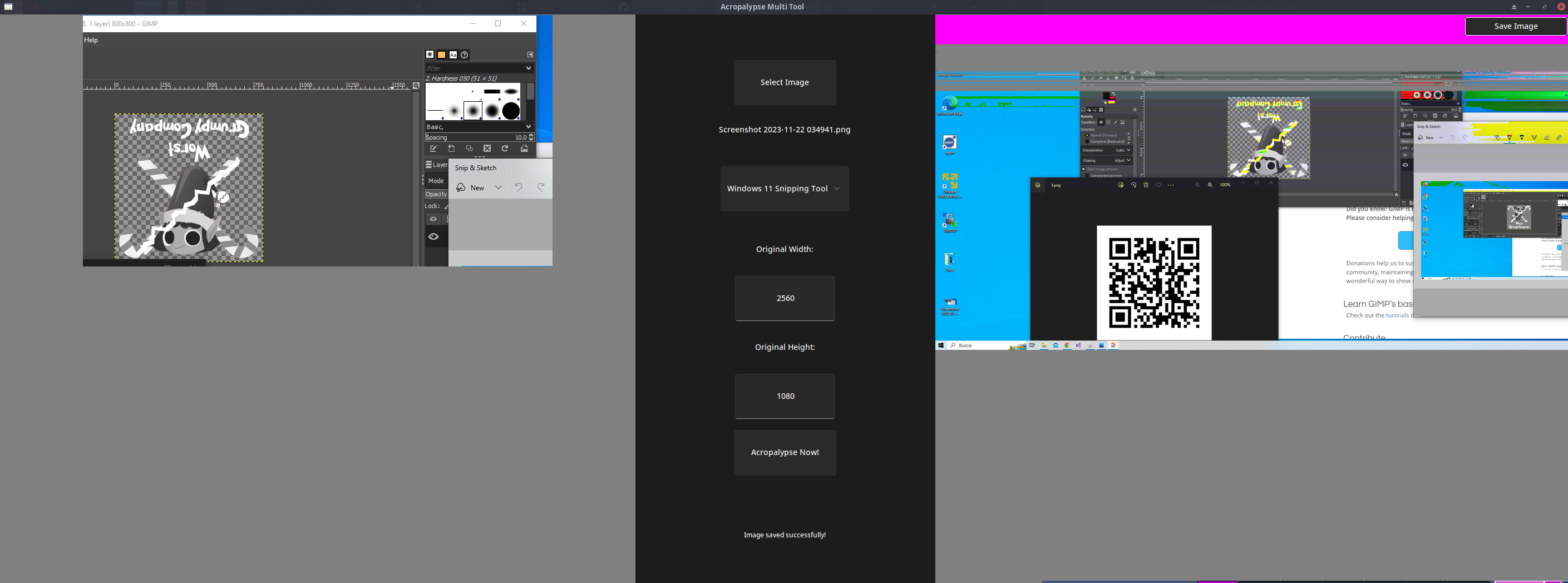
And lastly, I checked the image size of one of the other screenshots which appeared to not be edited or cropped. Then I inserted the image, the original image size (2560x1080) and voila! We have the key!
https://tryhackme.com/jr/armageddon2R
You can find a walkthrough of the room here.
Fourth Side Quest Challenge Key
The Fourth Key was the easiest to find. The key was “hidden” in Advent of Cyber’s Day 20 task.
In a nutshell, to retrive the key, all you need to do is to follow the instructions and restore the original conent of the .gitlab-ci.yaml configuration file.
Once that’s done, you can find the key on the page on port 9080:
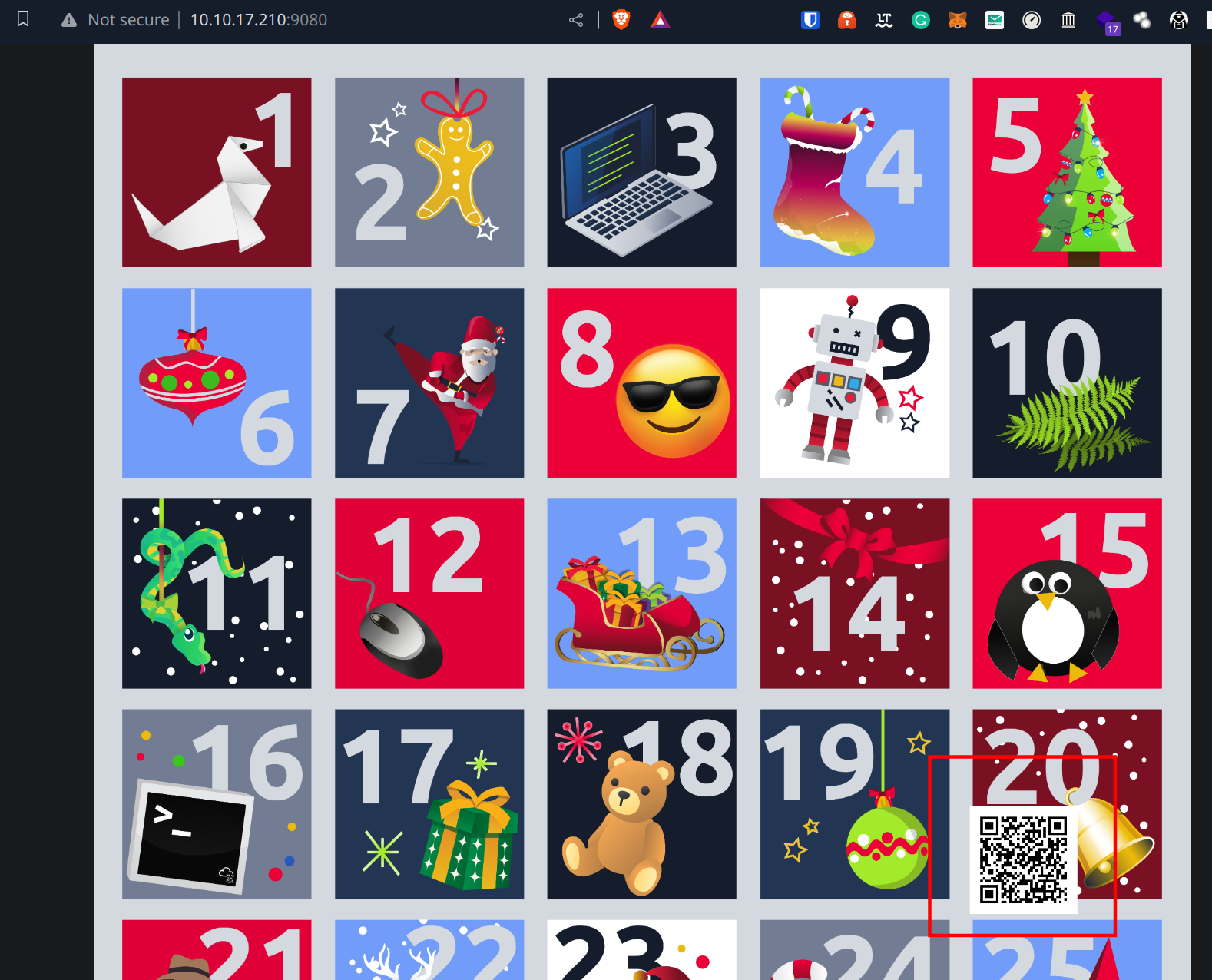
https://tryhackme.com/jr/surfingyetiiscomingtotown
You can find a walkthrough of the room here.
Conclusion
The process of finding the Keys to the actual rooms was a different experience as it is with challenges in different arias like OSINT WebAssembly and Markup vulnerabilities.
I personally found it very interesting, and I learned a lot.
I hope you found this post interesting and useful! 😄
If you are interested in the solutions for the actual rooms, you can find links to the writeups below: